video transcript
I'm gonna show you the most popular way to hack a website where you can
steal private information, hijack accounts, take over web pages and
other illegal things to get you thrown in jail
HOLD ON!
This isn't for illegal activity, it's for educational purposes only.
Notice, the lights are on, I'm not wearing a hoodie and I don't even
have a Matrix-themed terminal.
So there's NO crime goin' on here.
You have to promise me you'll use this information for GOOD and not
EVIL.
So when you're ready, this is the recipe for the basics of Cross-Site
Scripting.
Hello, world! I'm Jesse from Chef Secure. Cross-Site Scripting, or
XSS, is a security vulnerability in web applications That allows evil
hackers to inject their own code inside a web page.
Yep. That's bad.
With the power of scripting, cybercriminals can use your web
applications to steal passwords, install malware or WORSE...
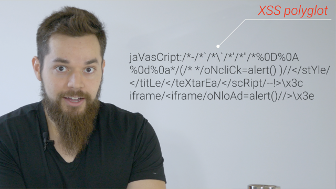
The first step in Cross-Site Scripting is to inject a script element
into a web page.
Now, web pages are built using HTML, which uses tags to create
elements.
Yep. There are a lot of 'em.
Let's get started. Go to the Script Injection example for this recipe
below, and pause the video when you need to, so you can follow along
and gain hands-on experience rather than just sitting there all
awkwardly, watching me do everything by myself.
You can see that when you type something in and click the UPDATE
button, it gets rendered on the page. So if you add more HTML, what do
you think would happen?
Open an HTML tag using less-than and greater-than characters
surrounding an element name, like p for paragraph.
Then add some content, and then add a closing tag after that – which is
just the same as an opening tag only there's a slash in front of the
element name.
Then click the UPDATE button.
You see that instead of writing text, you actually changed the HTML of
the web page by adding a new paragraph element.
While simple, this is very, very powerful, because JavaScript controls
the web page. And if you can inject a script element instead, you now
control exactly what happens in the browser.
And THIS is how XSS works.
So go ahead and inject script tags this time.
Start with your opening script tag, followed by your closing script
tag. Now for the content that goes inside...
This, my friends, is where we enter the f****d up world of JavaScript.
(phone buzzing) (phone buzzing)
WONDERFUL world of JavaScript!
Javascript can be... confusing at times. But what it does well, it
does EXCEPTIONALLY well like letting you hack websites or...
making them more INTERACTIVE.
Performing actions in JavaScript is like any other programming language
where you just call functions. You can do this by typing the name
followed by parenthesis.
And anything that goes inside the parenthesis gets passed as data, or
arguments, that the function can use.
AND like other programming languages, you can set values using an
equals sign.
Right now, try calling the alert function within your script tags.
So type in alert followed by parenthesis then click the UPDATE button
and watch your script execute.
Because you see this alert pop up, it means that your script was
injected into the page successfully and ran due to an XSS
vulnerability.
While you're at it, get some practice with arguments as well. So type
in the number 1 to the alert function. Click the UPDATE button and
you'll see it alert 1.
Or pass in text surrounded by either single or double quotes to make a
string, and you can alert something you really love.
I'm going to alert food.
Because I love food.
I'm always thinking about –
WAIT A SECOND!
CHEF? Secure...
Alerting is the most common function used by both cybercriminals and
security researchers alike to find vulnerabilities in websites.
Now keep in mind that the alert function is just a placeholder showing
that a script can be injected. And once a vulnerability is found an
attacker can easily replace this with a malicious exploit that causes
much more damage.
Consider something simple: instead of alerting in our example, let's
just destroy the whole web page by removing all the HTML.
In JavaScript, document.documentElement.innerHTML contains all the HTML
of the web page, so just change it by setting it equal to an empty
string.
In our example, if we type that in:
Click the UPDATE button and... it's gone.
I'm gonna show you more about how cybercriminals can exploit websites
in a later recipe, but if you're just testing for vulnerabilities, an
alert is really all you need most of the time.
So from here, what you really need is just to be creative and explore
so you can find more vulnerabilities. Say you need to type in
something in a website, such as a username or a status update, there's
always a chance that it could contain an XSS vulnerability, so it's
worth a shot.
Of course websites do have protections against XSS, some of them even
built directly into the frameworks on which they're built. But despite
this, and despite the frameworks being around for several years, the
number of XSS vulnerabilities is still rising like crazy!
And that's because writing secure, resilient code can be quite tricky
at times. And even with automatic protection, you can still screw
things up pretty badly.
Trust me.
I've done it more than once.
And I'll do it again, I promise!
But that's the point of having defense in depth , which I will teach
you as we go along in this course.
But mistakes happen, so let's look on the bright side: at least there
are plenty of vulnerabilities to find and fix before cybercriminals can
come and hack your application.
Wait, that's not comforting at all...
But that's all the time I have for now. Good bye, friends.